Compliance and security are critical for every organization, regardless of its industry. They help prevent massive penalties, build credibility and earn the trust and confidence of customers.
However, given the complexity of today’s IT ecosystem, managing compliance is not easy. Additionally, there are different environments, including development, testing, staging and production — which further complicates matters.
Implementing new features to improve product efficiency, adding new resources to the environment and managing multi-system integrations can also introduce more complexity, misconfigurations and threats.
This is where system hardening comes into play. In this blog, we’ll uncover what system hardening is, its relevance, what the benefits are and how Progress Chef supports DevSecOps teams in hardening heterogeneous systems with efficiency.
What is system hardening?
System hardening is the process of strengthening security across different technologies in an organization’s IT ecosystem. System hardening aims to mitigate cyberattacks by minimizing the attack surface and reducing vulnerabilities in servers, applications, firmware and other areas. The term “system hardening” can include server hardening, network hardening, app hardening, database hardening and more.
Considering the impact that cyberattacks have on organizations, system hardening has gained significance as a strategic defense initiative. It involves closing the gaps that attackers frequently use to exploit systems and gain access to sensitive data.
Why is system hardening important?
System hardening minimizes the attack surface of systems, reducing the hacker’s chances of gaining access to the environment. It enhances the system's resilience, fortifying it against unauthorized entry from individuals with malicious intent. The process involves checking the IT environment for misconfigurations and incompatibility issues and then facilitating the audit process. Misconfigurations pose a significant risk, potentially exposing an organization's IT ecosystem to cyberthreats. Microsoft's research indicates that 80% of ransomware attacks can be attributed to software and device misconfigurations.
Adding new servers, users or applications creates opportunities for vulnerabilities to emerge. Managing configurations manually in organizations with numerous assets and diverse configuration options can lead to errors. Given the inevitability of such events, it is crucial to prioritize secure configurations and manage continuous compliance in the ever-changing infrastructure ecosystem.
Achieving this requires implementing automation tools that continuously monitor and audit the organization's heterogeneous IT assets and promptly address any deviations that arise.
How can system hardening help in meeting compliance standards?
Depending on their industry and geographical location, organizations are subject to diverse regulations and standards like the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). System hardening plays a crucial role in demonstrating compliance with these regulations, thereby reducing the risk of potential fines and legal repercussions.
A prevailing trend among organizations is to base their system-hardening efforts on the benchmarks provided by the Center for Internet Security (CIS). These benchmarks represent a collection of best practice configuration standards that have been developed through consensus among various cybersecurity experts. With over 100 benchmarks available, encompassing a wide range of operating systems, server software, databases, desktop software, printers and public cloud infrastructure, the CIS benchmarks offer extensive coverage. Due to their broad applicability and high level of authority, they serve as an excellent starting point for organizations looking to enhance the security of their systems through hardening measures.
Hardening your systems using Chef Compliance
Chef Compliance and Chef Cloud Security solutions use CIS and Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIG) benchmarks to audit and remediate misconfiguration in on-premises and cloud environments to help make IT ecosystems more secure and compliant.
With Chef Compliance, you can:
Chef Cloud Security and Chef Compliance Key Features
Chef Compliance makes it easier for DevOps practitioners to help maintain and enforce IT compliance and security across the enterprise. Chef Compliance uses standards-based audit and remediation policy content and easily tuned baselines that can adapt to your organization’s internal requirements. In turn, Chef Compliance helps improve visibility and control of the security and compliance posture across heterogeneous environments.
Chef Compliance supports all stages of the compliance workflow:
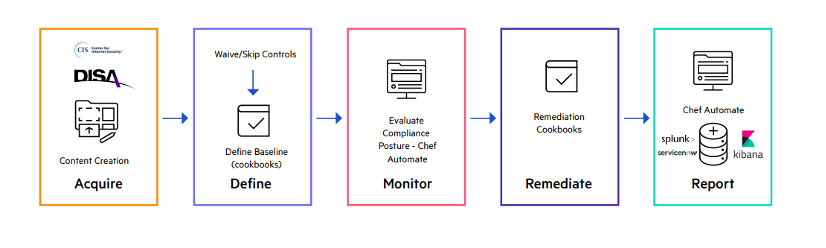
Chef Compliance delivers curated content for audits, remediation and desktop configuration based on CIS-certified benchmarks or DISA STIG. It continuously maintains and updates the Chef Premium Content library. When a new or updated profile is identified, it quickly certifies the content and makes it available for content subscribers.
The collaboration capabilities of Chef Compliance allow all parties involved in both the pre-production development process and production operations to see the real-time compliance status of any infrastructure. Automating the remediation process helps close the loop between audit and remediation to support continuous compliance in the enterprise. New remediation functionality and trusted, standards-based content make it easy to remediate issues uncovered during audits without writing any code.
Chef Cloud Security empowers IT Teams to continuously monitor cloud accounts and container platforms for security misconfigurations. Users can align internal/external regulation at scale to achieve more consistent, unified multi-cloud security using a coded approach and extensive community support.
Chef Cloud Security helps facilitate continuous security and compliance in the cloud through audits based on industry standards and benchmarks like CIS and DISA. Users leverage Chef InSpec to customize their own profile and usage to validate the controls for cloud and on-premises systems.
Conclusion
System hardening is a vital component for organizations in managing the security and compliance of their diverse IT ecosystem. It also plays a key role in helping achieve compliance with industry standards and regulations. Organizations often turn to established benchmarks like those provided by the CIS as a foundation for their system-hardening efforts. Chef Compliance emerges as a valuable tool in this endeavor, leveraging benchmarks such as CIS and DISA STIG to audit and remediate misconfigurations. With features like compliance scans, benchmark-based remediation, exception handling and customization options, Chef Compliance empowers organizations to maintain and enforce IT compliance and security with greater ease.
Resources
Learn more about Chef Compliance
Whitepaper: Buyer’s Guide for Continuous Compliance Solutions in DevOps
This blog was prepared by Shua Matin in their personal capacity. The opinions or representations expressed herein are the author’s own and do not necessarily reflect the views of Progress Software Corporation, or any of its affiliates or subsidiaries. All liability with respect to actions taken or not taken based on the contents of this [blog/article/white paper] are hereby expressly disclaimed. The content on this posting is provided "as is" with no representations made that the content is error-free.

.jpg?sfvrsn=3b75d702_0)
