Many cloud vendors tout their cloud solutions as secure from the get-go, with their experts keeping tabs on the applications and services they provide. Some of this is true. Good cloud vendors do offer certain measures of protection for their offerings.
Those vendors do make the cloud relatively safe, but the fact is that the cloud today is a security minefield and the vendors’ best efforts usually only go so far.
The cloud is arguably the root of most breaches. “Gartner predicts that through 2025, more than 99% of cloud breaches will be traced back to preventable misconfigurations or mistakes by end users,” Venturebeat reports.
Cloud Security Posture Management (CSPM) is the answer to many cloud security woe. Here are six things to know about CSPM:
1. What is Cloud Security Posture Management (CSPM)?
“Cloud Security Posture Management comprises all the security and compliance management tools an enterprise uses to maintain a secure multi-cloud environment without any misconfigurations or vulnerabilities,” the
What is Cloud Security Posture Management? page explained. “The CSPM approach begins by first analyzing your current cloud security posture and then devising a strategy and set of best practices that
improve your cloud security posture and maintain it continuously via management.”
The good news is that there are specific CSPM solutions to help get the job done and maintain high levels of CSPM. Gartner argues that CSPM solutions, “continuously manage IaaS and PaaS security posture through prevention, detection and response to cloud infrastructure risks. The core of CSPM offerings applies common frameworks, regulatory requirements and enterprise policies to proactively and reactively discover and assess risk/trust of cloud services configuration and security settings. If an issue is identified, remediation options (automated or human-driven) are provided.”
2. The Role of IT in Cloud Security: The Shared Responsibility Model
While cloud vendors secure key portions of their offerings, IT is still responsible for configuration, security monitoring, securing identities, devices, and passwords, blocking data leakage and preventing insider hacks. This is where shared responsibility comes in.
Microsoft is a key cloud provider and shared responsibility proponent. Here is what the company says about SaaS applications, one of many cloud service types that must be protected. “For SaaS solutions, a vendor provides the application and abstracts customers from the underlying components. Nonetheless, the customer continues to be accountable; they must ensure that data is classified correctly, and they share a responsibility to manage their users and end-point devices,” Microsoft argued. “For SaaS solutions, a vendor provides the application and abstracts customers from the underlying components. Nonetheless, the customer continues to be accountable; they must ensure that data is classified correctly, and they share a responsibility to manage their users and end-point devices.”
Microsoft believes IT must consider security before adopting cloud solutions. “It is important that customers consider how security and compliance are managed by the cloud solution provider (CSP) who will enable a safe computing solution. In addition, many organizations that consider public cloud computing mistakenly assume that after moving to the cloud their role in securing their data shifts most security and compliance responsibilities to the CSP,” the software giant explained in its Shared Responsibilities for Cloud Computing whitepaper. “Cloud providers by design should provide security for certain elements, such as the physical infrastructure and network elements, but customers must be aware of their own responsibilities. CSPs may provide services to help protect data, but customers must also understand their role in protecting the security and privacy of their data. The best illustration of this issue involves the poor implementation of a password policy; a CSP’s best security measures will be defeated if users fail to use complex or difficult-to-guess passwords.”
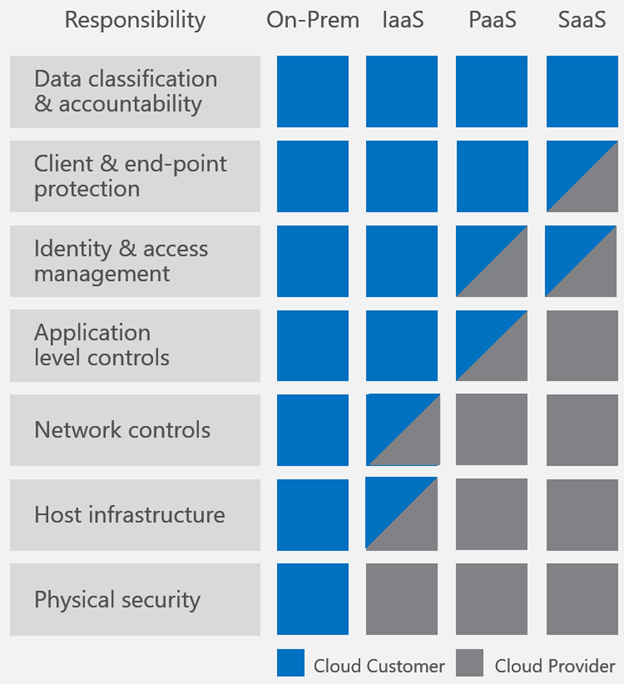
This chart shows what security areas IT is responsible for at each level of the cloud services stack.
3. Why You Shouldn’t Live Without a CSPM Solution
In the early days of the cloud, enterprises applied an array of tools to secure cloud data and services, which is still very much the case. However, having a dedicated CSPM solution offers an overview of key cloud applications and services and is the
only way to determine, manage and maintain a robust cloud security posture.
A proper CSPM solution will protect all cloud types, including multi-cloud/hybrid environments.
Here are items a five CSPM addresses, according to our extensive CSPM glossary page:
- “Simplifies multiple cloud-based services and tools into one
- Makes managing and maintain security and compliance easy
- Makes implementing Cloud Governance more easy
- Reduces vulnerabilities and legal threats associated with misconfigurations
- Ensures continuous compliance for cloud and cloud-native Apps.”
Other benefits include:
Automation
IT today is looking to have basic processes automated and performed safely. Here a CSPM solution cuts the time and effort of development and security teams to identify, audit and remediate misconfigurations and other security risks.
Evidence
While it is tough to map your cloud infrastructure to compliance and regulatory standards, internal security policies and relevant security control frameworks, this is the only way to avoid breaches and fines. A CSPM offers this mapping while easing the gathering of evidence for security audits.
Reporting & Alerting
Your CSPM solution should create actionable reports of your overall cloud’s risk posture and offer deep dives into specifics. IT, DevOps and DevSecOps should get alerts to risks so an investigation or remediation action can be performed immediately.
Securing Cloud, Multi-Cloud and Hybrid
The cloud environment is becoming increasingly complex and security complexity rises along with it. “Adaptability and ease of deployment drove the shift to cloud-based services and applications. But this shift has brought its share of vulnerabilities and threats. As a result, securing multi-cloud/hybrid environments and maintaining a consistent security posture is challenging for most enterprises,” the CSPM glossary page explained.
Visibility
A good CSPM solution should have a centralized dashboard containing actionable metrics. This dashboard provides a unified view of the enterprise’s cloud infrastructure security posture across multiple cloud environments and accounts.
A good CSPM provides visibility across your entire cloud infrastructure and offers compliance and security all in one solution. The same CSPM solution automates critical processes and provides a 360 view and control over an enterprise’s application and service environment, removing the risk of misconfiguration, vulnerabilities and compromised security.
4. CSPM Core to DevOps Best Practices
DevOps professionals are concerned with the security of their applications throughout their entire lifecycle, including iterations which occur frequently due to Agile methods. CSPM should be baked into all stages of the application development process, with security tracked, managed and guaranteed through continuous monitoring.
When it comes to CSPM, the earlier the better. “A core tenet of DevOps is to do things at the point where it costs the least amount of money to fix. The earlier you can identify issues in the process of creating resources, the faster you can give feedback to the people who are creating and consuming resources in the cloud. DevSecOps solutions such as CSPM, IaC scanning and Policy as Code help organizations merge these processes and get people on the same page,” claimed the For Better Security and Efficiency, Add CSPM to DevOps Processes blog.
5. Monitor Your Cloud Security Posture
You can’t have CSPM without monitoring your cloud assets and do so continuously and deeply.
As our glossary explains, this monitoring can include:
- “Tracking individual applications and cloud infrastructure components
- Showing whether services and other resources are up of down
- Tracking state of resources, such as their level of update
- Detecting misconfigurations”
Of course, monitoring doesn’t help much unless IT and stakeholders understand what is found, which is done through alerts for important problems and reports providing a macro and micro view of the state and activity of your cloud resources.
6. Use CSPM for Bullet Proof Configurations
We mentioned that Gartner believes “99% of cloud breaches will be traced back to preventable misconfigurations or mistakes by end users.”
CSPM prevents these configuration errors by enforcing that only proven proper configurations are applied, and when misconfigurations slip through, the CSPM scans finds them so they are quickly repaired. “Proactive scanning with CSPM makes it possible to identify misconfigurations for remediation. However, the upstream pipelines and provisioning process that created the resource should also be addressed. IaC templates and resources should be scanned for misconfigurations in the pipeline, and appropriate policies should be set so developers are made aware of a misconfiguration even before they provision a given resource in the cloud. This is often referred to as Policy as Code,” the For Better Security and Efficiency, Add CSPM to DevOps Processes blog explained.



